Introduction of Wireshark
CCIE Dumps CCIE Dumps CCIE Dumps CCIE Dumps CCIE Dumps CCIE Dumps CCIE Dumps
Many students are interested in wireshark, so we come to see together.
- 1. Dnowload and installation of wireshark
Wireshark, a free package analysis software, can be accessed through the official website https://www.wireshark.org/download.html to download and install, supporting multiple platforms such as Windows, Linux, macos. Wireshark is powerful and easy to install. It is useful for us to master its usage that can help us intuitively and profoundly understand the working principle of network protocol and clear troubles in the later work. What`s more, if interested in usb, bluetooth package, you can check on all of the optional installation while installing software, in order to obtain richer functionality.
- 2. Start packet capture
When you open the wireshark the network card list (as the following picture) will appear. YOU can usually connect the network card in the switch to the caught equipment to capture packages. which card want to capture the packets directly double-clicking is ok to capture the packets, the way that is simple and convenient (Here I use my wireless network card to demonstrate).
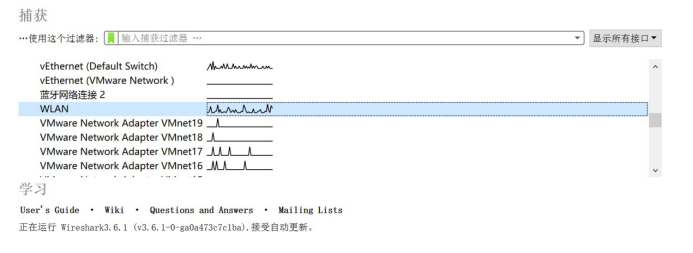
Because of big amount of data in the network we can click the capture button in the upper left corner to stop capture after getting what we want. During the process we need to button three buttons, which, in turn, is start, stop, recapture.
Now we look at package list.
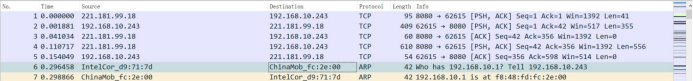
“No” is on behalf of the serial number, which represents the the number of captured package; “time”is relative capture time; “source” is package source address; “destination” is destination address; “protocol” is protocol type that parses out package;”infor” is summarized packet information.
According to the above information we can choose what we want to analyze, taking a HTTP package as an example.

Clicking the package we can see several folded information. The closer to the above is closer to the physical layer; the closer the bottom is closer to the application layer. We open in turn and see what information can be accessed.

First seen is the physical information, including information about physical interface, the length of the frame, as well as the state of the frame.
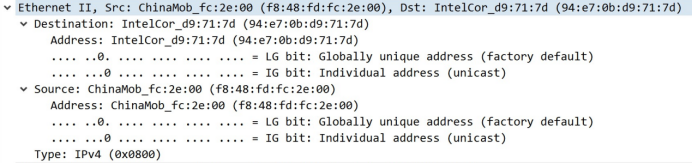
The next is the second layer, including Ethernet frame encapsulation type, the source MAC address and the destination MAC address. Because wireshark is a built-in analysis capabilities catching tool, it can help to mark the useful fields, such that the MAC address in the figure is a unicast address (the MAC address of the eighth for unicast or group cast, 0 for unicast, 1 for group cast), which is clearing and convenient for catching. So you can find the corresponding fields in the following hexadecimal area to analyze.
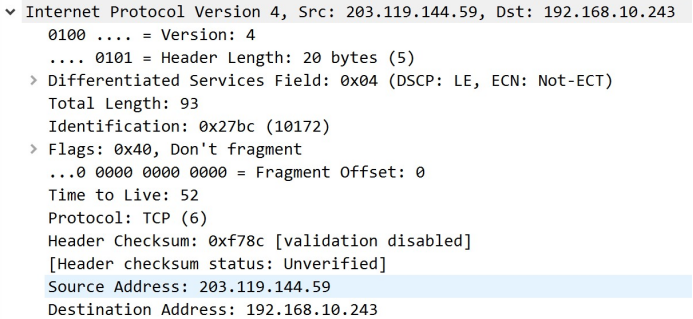
Next is three layer, including the IP version (ipv4), head length, DS Field, the head check and the source IP address and TTL Field that we always review after first glance.
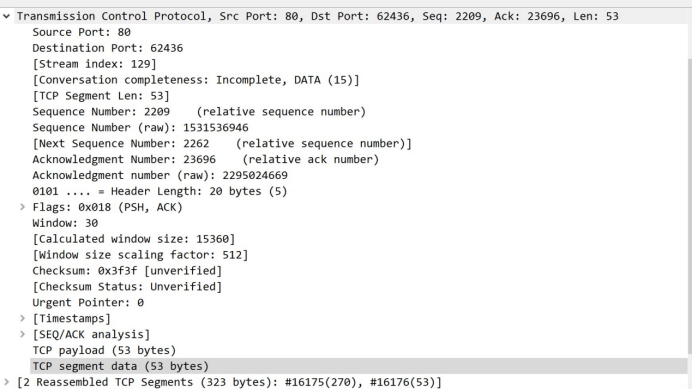
And then we explain the transport layer. Here that we pay more attention to is the transport layer protocol, source port, section size, seq Number, sign information and payload size, etc.
Figure shows the transport layer protocol for TCP, the source port 80 proved to be an HTTP related package. And TCP segment length is 53 bytes, and ACK is setted ( if you want to find an ACK, you can minus one in the seq number to search which package is responsed by the ACK ).

The upper-layer protocol as a network engineer usually we are not too concerned about, but sometimes there is a demand we can also open and analyse, such as here we see HTTP return a 200, so we can know it is a normal response package. This package is caught in some projects on the upper application we need to do a firewall or the server may need to, fortunately wireshark to related functions are also supported.
CCIE Dumps CCIE Dumps CCIE Dumps CCIE Dumps CCIE Dumps CCIE Dumps CCIE Dumps
So we know the basic operating, but in the complex network environment, sometimes it seems to look for a needle in a haystack when we try to find what we want in so many date packages. So is there any way I can use to quickly find the package, or is there any operations is helpful to catching analysis?
Commonly used filter ways of Wireshark
IP address filtering is used to show the corresponding IP address packets, at the same time IP. SRC and IP.DST for more detailed designation for suitable for source IP or destination IP. Similarly eth. addr is used to show the corresponding MAC address package, and eth.src and eth.dst show we specifically want MAC source or destination MAC.
Protocol filtering: if we want to catch a special port, we can use tcp.port or udp. Port to filter; if we want to filter a particular protocol we can also enter the name directly; if we want to filter out ospf packet,we can directly input ospf in the filter.
After knowing about the way of filtering, let us try to practise in hand to grasp quickly.
First of all, we try to filter the source IP 192.168.10.243, and destination MAC for f8:48: fd: fc: 2 e: 00 packages.
Next, we use the DNS port to exclude the DNS message.
Next, we add all the broadcast message.
After the above practice, we are familiar with the use of address, protocol, logical operators, so we try to network within the next packet according to certain characteristics of a grab
First, we need to filter the ospf package.
Then we need to find all the message associated with second kind of lsa.
Opening a LSU message we can see there are packages with second layer LSA were left, while the rest of it were filtered, which is convenient and faster to find we packages we need to contrast.
After reading today’s share many friends are ready to do it yourself. Hoard our lab to know more information about network engineers.
Introduction of Wireshark
CCIE Dumps CCIE Dumps CCIE Dumps CCIE Dumps CCIE Dumps CCIE Dumps CCIE Dumps